
Traveling Productivity with Technology
Traveling Productivity with Technology Packing for trips can be frustrating because there’s always the chance that you’ll pack either too much or too little. This

5 Cloud Apps Small Businesses Should Love
5 Cloud Apps Small Businesses Should Love Businesses of all types have looked to the cloud as a way to receive the goods and services

Tip of the Week: Using Less Data on Android
Tip of the Week: Using Less Data on Android Mobile data is extremely important to the productivity and efficiency of modern businesses–especially when employees and
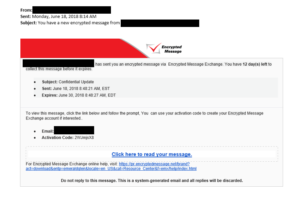
The Anatomy of a Phishing Attempt
The Anatomy of a Phishing Attempt The Anatomy of a Phishing Attempt Recently, a client called us, concerned that their email accounts had been hacked

BaaS Lets You Take Decentralization for a Test Drive
BaaS Lets You Take Decentralization for a Test Drive One of the biggest problems with emerging technologies is the fact that it can be very

Technology Basics: Wizard
Technology Basics: Wizard The word “wizard” may not seem to have much to do with computing, besides calling someone a “computer wiz.” However, there is

Your Backup Needs to Meet Some Prerequisites
Your Backup Needs to Meet Some Prerequisites There is always the constant threat of data loss looming over your business. Even though the idea might

Surveying the Damage of Meltdown and Spectre
Surveying the Damage of Meltdown and Spectre At the time of this writing, it has only been about a half a year since the Meltdown

Tip of the Week: What You’ll Need to Leverage BYOD
Tip of the Week: What You’ll Need to Leverage BYOD Bring Your Own Device has a lot of benefits for businesses, chief among them being


