The Anatomy of a Phishing Attempt
The Anatomy of a Phishing Attempt
Recently, a client called us, concerned that their email accounts had been hacked and a phishing attempt was in progress. Fortunately, one person was smart enough to ask the questions which ultimately saved their company $187,000.
The Cast of Characters;
Company President (“Pres”)
Company CFO (“CFO”)
Internal financial analyst (“FA”)
Internal IT (“IT”)
The Timeline;
June 26, 2018
10:57AM– Pres sends email to FA telling her to send a wire transfer in the amount of $187,000*. The message states that this amount constitutes a 60% deposit for a transaction.
FA replied back to Pres and copying CFO, asking if she should proceed with the transfer.
FA received an email back from CFO approving the transfer**.
In the meantime, FA called Pres to confirm this transfer, and was told this was not a legitimate request.
FA then replied back to CFO, again telling her she talked to Pres and that this was not a legitimate request***.
12:25PM – IT put in a help desk ticket for Ashton to take a look.
Ashton investigated the link, then advised client to reset Pres email password as it was clear that President’s email account had been compromised.
1:40PM– Pres sends emails to all of his Outlook contacts, asking recipients to login to view an encrypted message. Login required recipients’ email credentials#.
2:05PM– IT finally resets Pres email password. Delay was due to not wanting to inconvenience the President of the company.
At this point, Pres email was blocked by Microsoft Office365 protection (large quantity of emails at one time immediately caused the account to be blacklisted) and Ashton received another helpdesk ticket from IT. She was unable to send from Pres email account. Nothing was showing in spam filter.
*The company President did not actually send the email asking for a wire transfer
** The approval for the wire transfer was not actually sent by the CFO. Rather, it was sent by the cybercriminal who was controlling inboxes owned by both the President and CFO.
*** The acknowledgement from FA to CFO stating that the wire transfer was not legitimate was never received by the CFO. Again, the person controlling the CFO’s inbox deleted the email before the CFO ever saw it.
#The company President did not actually send an email to all of his Outlook contacts. The bad actor controlling the inbox did this.
How It Happened
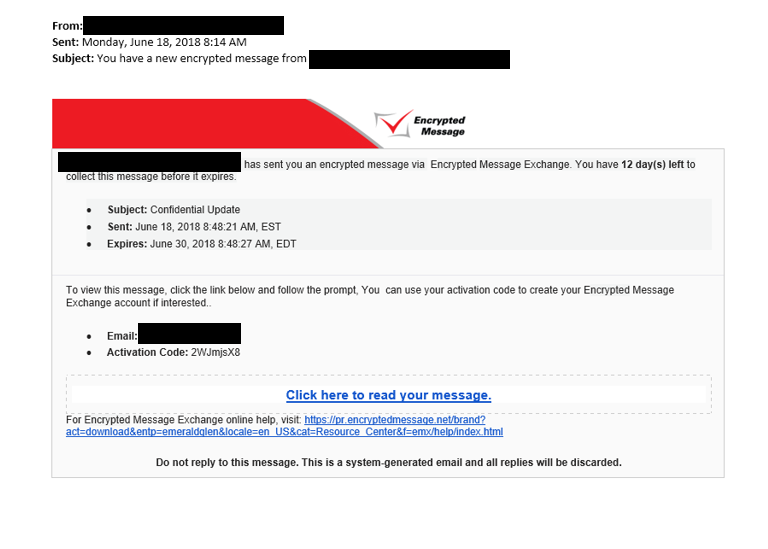
On June 18, 2018, the CFO received the below email from their General Counsel. The President received a similar email, also from General Counsel. Both Pres and CFO believed the email was legitimate, clicked the link, and entered their credentials.
What We Found and Resolved
Pres was no longer able to send any emails after being blacklisted by Microsoft Office 365. We (Ashton) were able to correct this through the Microsoft Exchange portal.
A rule had been created in the inboxes of both the Pres and CFO to automatically delete any internal emails they received. This meant that neither person would be alerted to any concerns of improper activity.
Numerous emails had been deleted, and then removed from the deleted file, theoretically preventing the owner of the inbox from seeing emails they’d received. However, some of these emails were indeed recoverable, allowing the Ashton engineers to piece together what had taken place.
All admin passwords were subsequently reset.
IT later found a spam email including a link that both Pres and CFO clicked. This link asked for Office 365 credentials, and both the Pres and CFO entered their account information, thereby giving the cybercriminal access to their inboxes.
Why was this not stopped by any sort of security solution (e.g. firewall, endpoint protection, spam filter)?
- The sender was legitimate
- The link was to a Google Doc
- The websites included were all legitimate
- No activity was initiated by a macro or executable file
In the end, it turned out that the General Counsel of Ashton’s client had fallen for the same phishing attempt two weeks earlier (on or about June 11, 2018). The cybercriminal had plenty of time to make numerous attempts at gaining user login credentials through ownership of the attorney’s inbox. Finally, on June 18, two contacts (that we know of, our client’s President and CFO) fell for the scam. That then gave the cybercriminal the chance to cast his net even further.
What does this prove? It proves that no matter how safe your network is (and this one is locked down with firewalls, endpoint protection, and spam filtering), it all comes down to your users. If your users aren’t aware of what to look for, and aren’t always on guard, you’re opening yourself up to huge problems. More importantly, it shows just how at risk a business is, and how quickly things can spiral out of control. Don’t be afraid to question the veracity and legitimacy of any email you receive, even if it is from a trusted sender. That one extra phone call might save you and your company a fortune.





